I have direct evidence Konstantin Pylinskiy is involved in the Inferno Drainer project. He’s a power user of the SaaS (Scam as a Service) platform, we know that for sure. There’s evidence that leads me to believe he might also be the ADMIN of Inferno Drainer or a key player in the ADMIN Group at Inferno Drainer as a developer.
This post will be a TWO part series. In Part 1, I’ll document what Inferno Drainer is, how it works, and the wallets directly associated with the Inferno ADMIN vs the Inferno CUSTOMER.
In Part 2, we’ll focus on Konstantin’s (konpyl) role in Inferno Drainer. I’ll show direct on-chain evidence linking him as a CUSTOMER and possibly as the ADMIN of Inferno Drainer.
Inferno Drainer’s History
Inferno Drainer launched in Feb 2023 as a Scam-as-a-Service platform. Commonly called “wallet drainers”, Inferno Drainer created a low barrier of entry for individual users to participate in phishing scams.
Inferno Drainer separated itself from other draining service competitors through ease of use, zero knowledge trust and the wide variety of chains supported.
The web3 Phishing industry became big business in 2023 with Inferno Drainer leading the way. In 2023 alone, Inferno Drainer was responsible for over $80 Million in stolen cryptocurrency.
After a short hiatus, Inferno Drainer came back with a vengeance in May of 2024. This year is looking to be the biggest year to date for phishing scammers.
The Shutdown
On Nov 27th 2023 the Inferno Drainer ADMIN shocked the world by announcing his retirement and putting an end to the Inferno Drainer project.
Why shutdown when you’re at the top of your game?
Many sleuths theorized that law enforcement was finally catching up to Inferno Drainer while others pointed the finger at new web3 anti-fraud technology like Blockaid significantly disrupting Inferno Drainer’s operations.
I have a completely different theory which I’ll discuss in Part 2!
Nevertheless, Inferno Drainer appeared to shutdown operations, at least to the majority of their customers.
Inferno “Reborn”
After 6 months of silence, Inferno Drainer announces its triumphant return on May 20th 2024. The telegram post was interesting as it mentions updates not only to the platform itself but changes in the staff and support.
With notable competitors like Pink Drainer announcing its retirement, the timing seemed right to steal the spotlight and bring back Inferno Drainer into the public consciousness.
The reality is Inferno Drainer never really “retired”. Instead, the platform made the business decision to keep a low profile while upgrades were getting implemented.
How Inferno Drainer Works
There are better articles out there that go into the details of the ins and outs of Inferno Drainer. Specifically, Group-IB’s Inferno Drainer article and the Goodbye Inferno Medium article do an excellent job explaining key findings within the platform itself. Nevertheless, here’s my own take of how Inferno Drainer works.
The Inferno Drainer team operates like a shadowy syndicate, offering customers a slick, user-friendly panel and a discreet Telegram channel for communication.
The client, equipped with these malicious phishing tools, copies and pastes the drainer code on websites promising free Airdrops or NFT mints. An army of fake or hijacked social media accounts promote the scam website on Twitter, Discord, search engines and other social media networks.

Unsuspecting victims stumble onto these carefully crafted sites and are tricked into approving malicious transactions. Once given approval, the Inferno Drainer assesses the victim’s most valuable assets and steals everything it can.
The stolen assets flow seamlessly into the criminals’ hands with about 20% funneled back to Inferno Drainer’s developers and the remaining 80% claimed by the client.
The Inferno ADMIN Wallets
Below are a listing of all of the confirmed Inferno Drainer wallets. I did not include any intermediaries associated with the main wallets. Those are endless!
Main Wallets
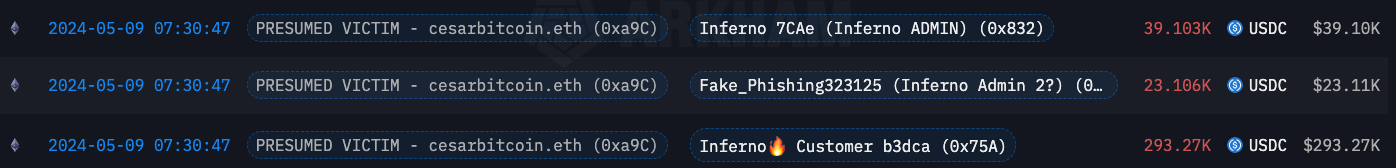
Above is how MOST Inferno Drainer phishing scams look on chain.
The VICTIM - 0x0D15c865c537683D797996EDdb5eF28e974B6F70 - has a theft that occurs on 9/3/24. About 20% goes to Inferno ADMIN, 80% goes to the Inferno Customer. The exact breakdown appears to be 82.5% CUSTOMER, 17.5% INFERNO ADMIN in this instance.
The Main Wallets are all owned by the Inferno Drainer ADMIN and show a clear 80/20 split of stolen assets. Well all except one, which I’ll cover in Part 2. The dates to the right are the timeframes in which the associated wallet was active in draining victims.
Below are examples of victims who lost significant assets to Inferno Drainer confirming the ADMIN wallets on chain.
Listing of Main Inferno ADMIN Wallets
0x29488E5fD6bF9B3cc98A9d06A25204947ccCBE4D (2/9/23 - 3/1/24)
0x53d0E4dAb3E125dd25EcfB24Ca610075Fa9bC8e1 (10/5/23 - 3/1/24)
0xAb4Db125e41BbE6175f1D516D922733263CbF2eC (12/1/23 - 4/1/24)
0xf672775e124e66f8cc3fb584ed739120d32bbaad (1/3/24 - 6/18/24)
0x8328D248B779AF15e894951853E1A236F3Eb7CAe (3/13/24 - 7/4/24)
0xfc4eaa4ac84d00f1c5854113581f881b42b4a745 (3/19/24 - 9/22/24)
0x84672CC56b6DAd30cfA5F9751D9cCAE6c39e29Cd (2/3/24 - 7/22/24) *More on this one in Part 2*
0x89297c81892016b0f979e4e6eE50e2Ad837cFA1A - (5/10/24 - 7/17/24)
0xaA862F977d6916A1e89E856FC11Fd99a2F2fAbF8 (8/21/24 - ACTIVE)
One interesting detail about the above wallets is a number of them were activated during the Inferno Drainer “shutdown” between 11/27/23 - 5/19/24. It’s clear through on-chain data that Inferno Drainer was very much active, but maybe limited in usage to a select few clients.
Inferno Drainer Money Laundering
It’s interesting to watch the change in money laundering tactics over time. I was able to trace out most of the Inferno Drainer transactions. The data is too numerous to list here, but I’ll give a summary.
During 2023, most of the txns use 1inch Protocol to bridge to Binance, Whitebit, OKX, HitBTC, or MEXC deposit addresses. The deposit addresses appear to be mostly swapping services connected directly into the exchange API. The most common asset swapped to is Monero (XMR).
Additionally, there’s numerous one-off deposits into FixedFloat, SimpleSwap, SideShift and ChangeNOW deposit addresses.
I did see a few Tornado Cash deposits from Inferno Drainer wallets in mid to late 2023.
In early 2024, Inferno wallets appear to change up tactics a bit by utilizing Stargate and Thorchain bridges in addition to 1inch. The ADMIN starts doing deposits into eXch and uses Railgun to launder some of the stolen cyrptocurrency.
The latest Inferno Drainer laundering tactics appear more brazen. In some instances, stolen funds go directly into eXch deposit addresses while other funds get laundered through Thorchain into BTC or LTC.
Inferno Admin Contracts
I’m not exactly sure the full details of what the below phishing contracts do. I believe they use the multicall function to verify the destination of the approved ERC20 tokens and NFTs. I’m sure there’s many more malicious Inferno Drainer contracts I did not list, but here’s a few.
0x0000db5c8b030ae20308ac975898e09741e70000 (Inferno Approvals Contract)
0x000037bB05B2CeF17c6469f4BcDb198826Ce0000 (Inferno Receiver Contract)
0x00003d1cEf5F30E34510198cB045E4ae0aa20000 (Inferno Contract)
0x000056c346441ef8065e56b0CDDd43fdEC100000 (Inferno Contract)
0x0000DAf60a1BECF1bD617C584Dea964455890000 (Inferno Contract)
0x0000a068e571c45d28d4c603876a59FC81e30000 (Inferno Contract)
Create2
I did want to bring one notable update to the Inferno Drainer Contracts that helps phishing websites bypass website security alerts.
Hot wallets like MetaMask maintain blacklists for known phishing domains and accounts. Before a signature is approved, the wallet verifies if the domain or account is blacklisted.
The Create2 function allows the prediction of the contract address before deployment on the blockchain. Uniswap leverages this function, for example, to create pair contracts on their DeFi platform.
The below is the formula used.
In other words, prediction of the contract address is possible with the deployer address, bytecode, and salt value.
Inferno Drainer abuses the Create2 function by generating temporary new wallet addresses for each malicious signature.
The Drainer is able to avoid wallet blocker blacklists with the fresh wallet address.
Most of Inferno Drainer’s recent phishing transactions leverage some form of Create2 exploit.
ENS Wallets
The ENS Wallets are all connected for the simple fact there is an ENS domain registered for each address. Only the inferno-drainer-4.eth contract has significant volume. All of the below wallets go back to the early days of Inferno Drainer.
0x8413c544095f7e69d4ad3bfcf4b77deedda0cc39 (inferno-drainer-1.eth)
0xfb4d3eb37bde8fa4b52c60aabe55b3cd9908ec73 (inferno-drainer-2.eth)
0x00001f78189be22c3498cff1b8e02272c3220000 (inferno-drainer-3.eth)
0x0000553f880ffa3728b290e04e819053a3590000 (inferno-drainer-4.eth)
I’m showing the first txn from inferno-drainer-1.eth was on 12/12/2022 which could theoretically be the start of Inferno Drainer. However, I couldn’t find any on-chain evidence of victims getting drained during that timeframe.
Almost all of the funds from inferno-drainer-1.eth and its intermediaries go into inferno-drainer-2.eth.
inferno-drainer-2.eth sends almost of its funds to two wallets, inferno-drainer-3.eth (contract) and Inferno F2eC (Inferno ADMIN).
Lastly, most of the funds from inferno-drainer-3.eth go to the inferno-drainer-4.eth contract where the cyrpto is laundered through Tornado Cash.
Early Inferno Drainer Admin Wallets
The way Inferno Drainer contracts were setup in the first months of launch may look completely different than they operate today.
I came across 0x3B638ce6044BD08c8768049ABB981E9Dd7D24141 which has direct links to inferno-drainer-2.eth and various other known Inferno Drainer wallets.
If this wallet is indeed an Inferno ADMIN address, it would put the launch of Inferno Drainer on 10/14/22.
Additionally, the below wallets also have connections to the early days of Inferno Drainer. They do appear to be phishing wallets of some sort, but it’s unconfirmed if they are indeed Inferno Drainer ADMIN wallets
0x1d05F69d14519a1c93007B468E30D5cb1f1658DF
0x075D9bbefAcb33b7b73Ab8559989776fA0107bB8
0x76A973d1D7C15F07Ef3E4729a2D370b15614444e
Telegram Chatter
Lastly, I wanted to include Telegram conversations from the rumor mill. The below conversations are unconfirmed intel on the entities behind Inferno Drainer.
The support contact of Inferno Drainer is “InfernoDrainerSupport” on telegram. I don’t believe this person is behind the creation of Inferno Drainer. He appears to be a hired gun who helps Inferno Drainer Customers.
Rumors have him as “folie” and “blade” based on conversations below.
The below conversations are all referencing a 55 Million DAI phishing attack on 8/21/24 that users claim was an Inferno Drainer backdoor.
A victim lost $55M while these scammers complained about the distribution of the stolen funds.























