I previously posted about a victim who had 1000 ETH stolen from their Coinbase account.
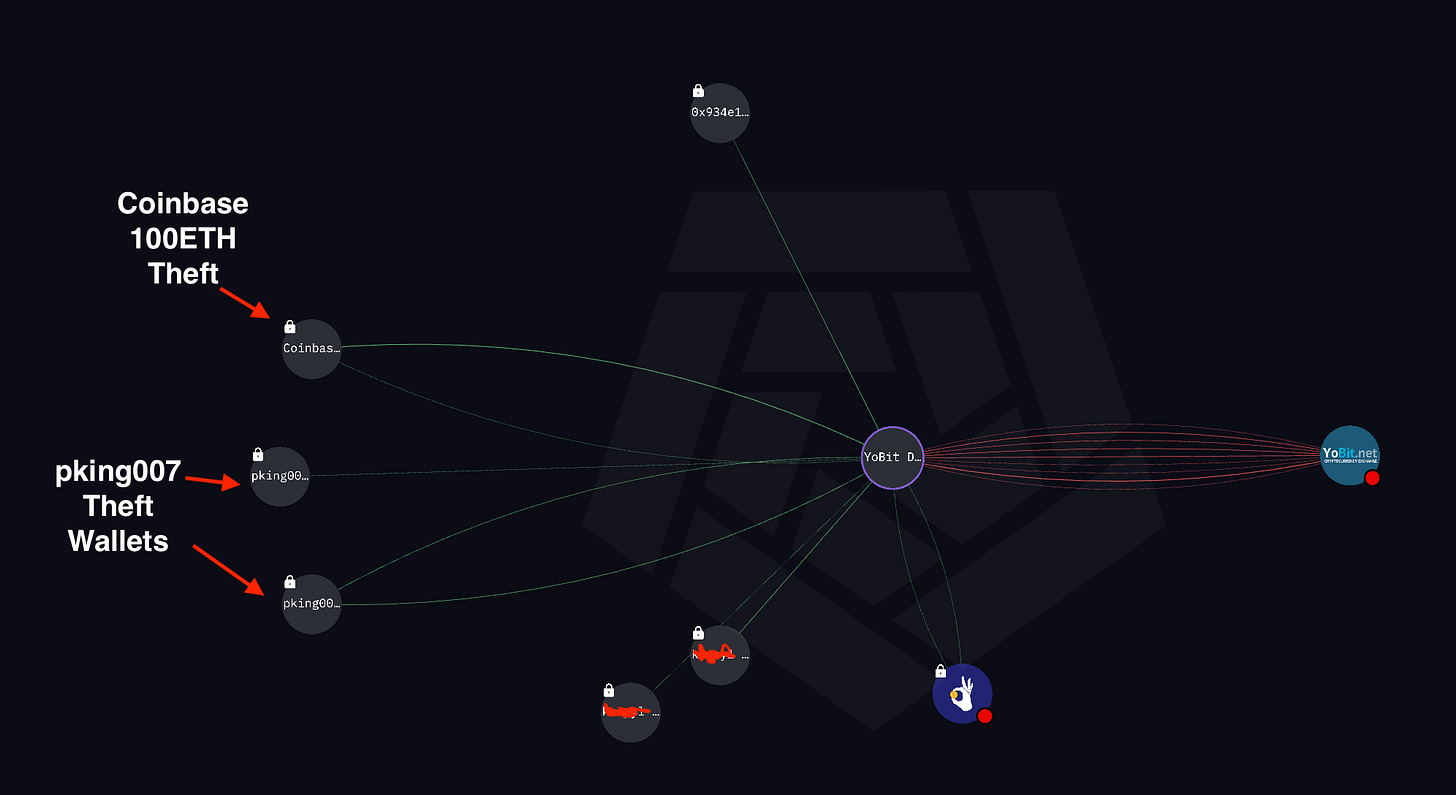
The 60K Ledger Live theft is directly connected to this hack through the shared Yobit Deposit address of 0x05a8fC18C8150cBD6cEc07621dE2aA7c426a21e6.
Above is connecting the pking007 thefts to the Coinbase 100ETH theft. The thefts happened around a similar timeframe.
pking007 Theft Wallets from image
0x0000000937e390bd7753B2B30a1b2d96154e9Aba
0x1111111bAeD9942134B1D3Ae62e9A67d049858eB
Coinbase 1000 ETH theft from image
0x2eF3cb572e0D114fCb6F0Afd80Dab7D43C7b1b4d
About 60K in BTC and ETH was stolen out of the victim’s Ledger Live device. Evidence points to Konstantin Pylinskiy aka konpyl as the individual behind this theft.
The victim unfortunately lost his life savings from this hack.
The Reddit Post
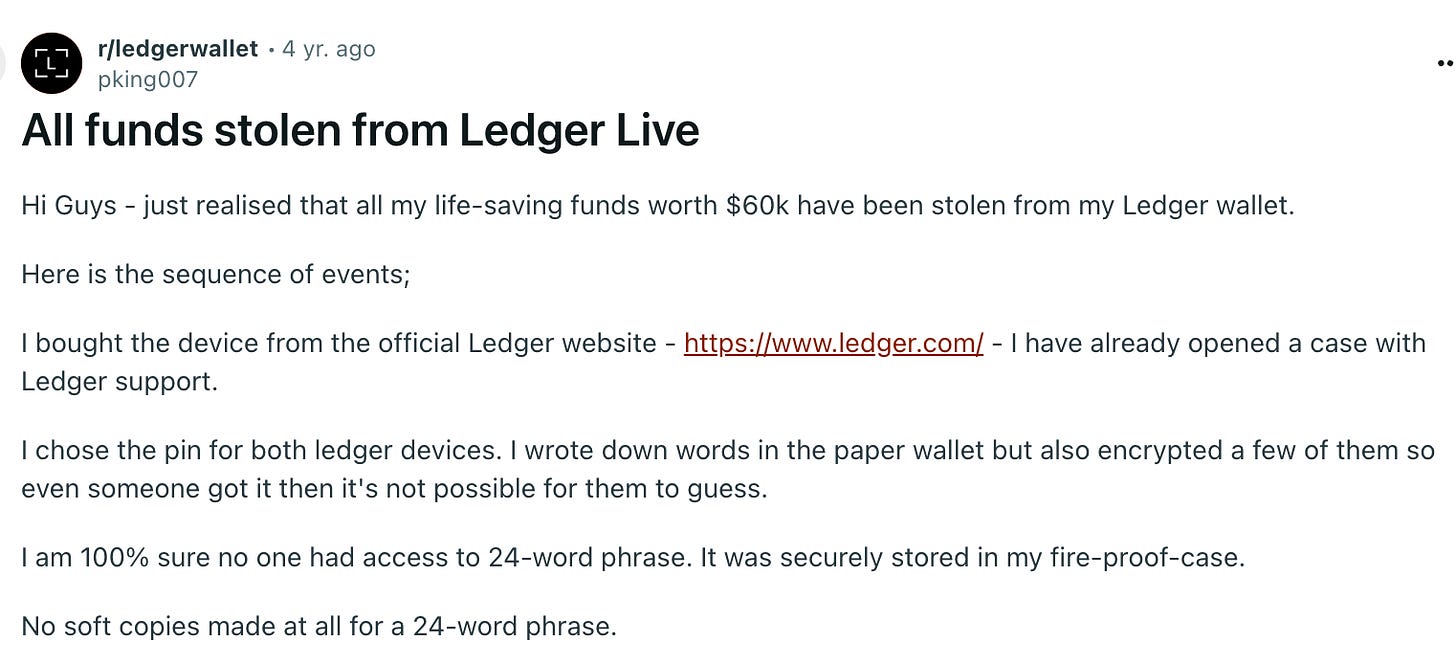
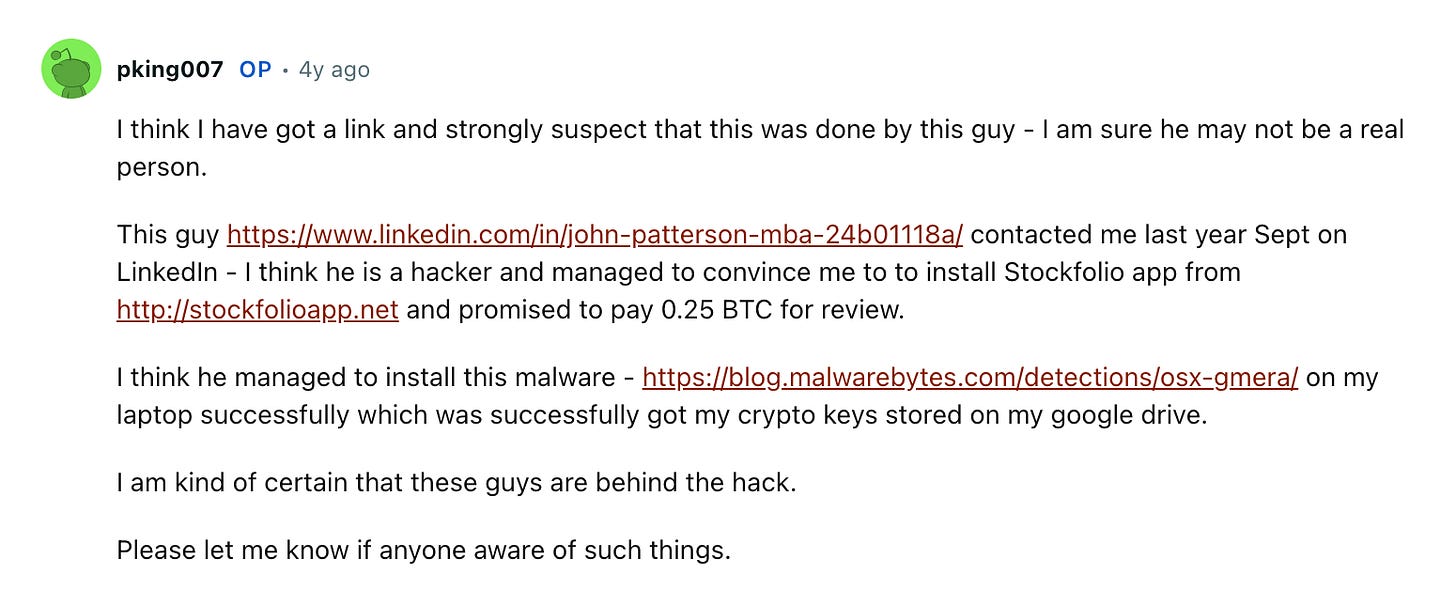
The victim, user “pking007”, posted the details of his 60K Ledger Live hack on Reddit that took place on 7/9/2020. I was able to easily connect Konstantin to this theft through shared deposit addresses and wallet activity.
The most interesting detail I picked up from the post was the victim mentioned the hack occurred within hours after updating Ledger Live. It’s also mentioned in the updated notes that he took a screenshot of his seed phrase at some point.
Based on the evidence, it’s my belief that the victim upgraded to a fake ledger live application.
Normally my first instinct would be to blame the picture of the seed phrase in the Google Drive, however this hack follows similar patterns to other fake wallets Konstantin has laced with malware over the years.
Specially looking at the theft address of 0x0000000937e390bd7753B2B30a1b2d96154e9Aba, I can see what appears to be numerous victims sending funds to this wallet over a similar timeframe.
Usually, a single seed phrase compromise doesn’t share wallet activity with other victims, but it’s not always the case.
Quadrig Initiative also has an interesting take on how the theft might of occurred based on the picture of the seed phrase stored on Google Drive.
They also believe malware was used.
According to Quadrig Initiative, it appears the Reddit user pking007 was tricked into installing a Malware called OSX.GMERA onto their Mac OSX by a stranger on LinkedIn who offered them 0.25 BTC for reviewing a fake Stockfolio application.
However, the theft took place, the victim can have some solace in knowing who was behind it.
Wallets in the Theft
The below wallets were used in the theft of 60K worth of BTC and ETH. I added these mostly for educational purposes and for anyone who wants to verify my findings.
Victim Addresses
0xA9697e7f7d67b3b47F84aD266ea9eA7d0882d52e - ETH
bc1qtdjsj8hpds4klqtxd0x362yfw36zuxy87x0zky - BTC
Main Hacker Wallets
0x0000000937e390bd7753B2B30a1b2d96154e9Aba - ETH
bc1qx47vyyuhktsve9pwyydpz3dklknedufckvd9ky - BTC
Additional Hacker Wallets Used to Launder the Funds ETH
0x08ef98409B19c366406DfC9704687Ac64C33910b (Zksync input wallet)
0xA2b35Dcc9A7486A001e8B833441829A799cAbC75 (Zksync output wallet)
0xaFA427e80DfFe73AE7f47773C31eE5dDB4D3954B
0x629ac5B1E9Ef886244a59f3cb22af9333759aE75 (475K mostly in ETH here)
0xdA06B6D56A5D3E9fC7f0212d5C14B97D4067971b
0x1111111bAeD9942134B1D3Ae62e9A67d049858eB
0x417beA1569aB6B15853A2fD12506297479143c18 (261K mostly in ETH here)
0x6577013f0b6af1D7b17cDdf16Dc272d73FC98958
0x39dC5D18c8853BB976003426485288aFDEfC6A7F
0xdcAA5DB8c1B1B4e5B8B4BF95a3c37D5CD0022510
Deposit Addresses
0x05a8fC18C8150cBD6cEc07621dE2aA7c426a21e6 - Yobit
0x8384A28405CAb394C2F684646110E6D4bC602D19 - Binance
0x21F6e8580A88AFa4EbB64AC2ECD614fC964F52C6 - Binance
0x11b074371fD7e7FBc4056CbB4868c99A9f0C4663 - Binance
0x19a9D78Fe07B0E0f89f95490B95d155Ae6861ae8 - Bitzlato
0x51F4d23A30ab6bD4237229494f4D4E32b07BE375 - FixedFloat
0xf09A2C93ee94f080FBc6aBB0bE67E77D9b87E80f - FixedFloat
0x6d279993Cf80C0dc8c22A9F54C46Bb173D509599 - FixedFloat
0xE862b853a08E4Ce4e8f0B3967AA4515653b47292 - FixedFloat
0x1fd1D56983F4eADe3A1977525E6FF7788007dC10 - FixedFloat
0xA7f68d9aBcd7A9Ab96DB59663d4100c50fa363f1 - FixedFloat
0xAE6701f48a5fD014Fb23Be067D63B5C4d446B9d7 - FixedFloat
0x6ef392c3C4678260C5500D9318B95928E174F254 - FixedFloat
0xE3D33A61d3E14278D471416b740A68373c5fC76d - FixedFloat
Additional Hacker Wallets Used to Launder the Funds BTC
bc1qp5md0humnrj6cejp3yee6gge0cjy3l9kv0pr9l
bc1qf29utv4ufjspvawexqqpzmu4rfnlswgpp3e34m
bc1qqr3f38ntweekux6dx332ka4xj6kz7uv05jt5e9
33NJQVDNiVvKbaZwNLEHm8FNzRDUGaNrFr
Deposit Addresses
355DJ271tGBzwsiNGUzhoVLJk8VjS5qfd2 - Kraken
1NW5xxmgmm51CV1LCziJGhrtadcSbhu7WS - Binance
1J8LvX8axhBGgmEqCEWYhyHrrpSEVNkEFV - Binance
Connection to Konstantin Pylinskiy
I mentioned above the victim who lost 1000 ETH through Coinbase. The same Yobit deposit address of 0x05a8fC18C8150cBD6cEc07621dE2aA7c426a21e6 connected both hacks and additional “konpyl” owned wallets.
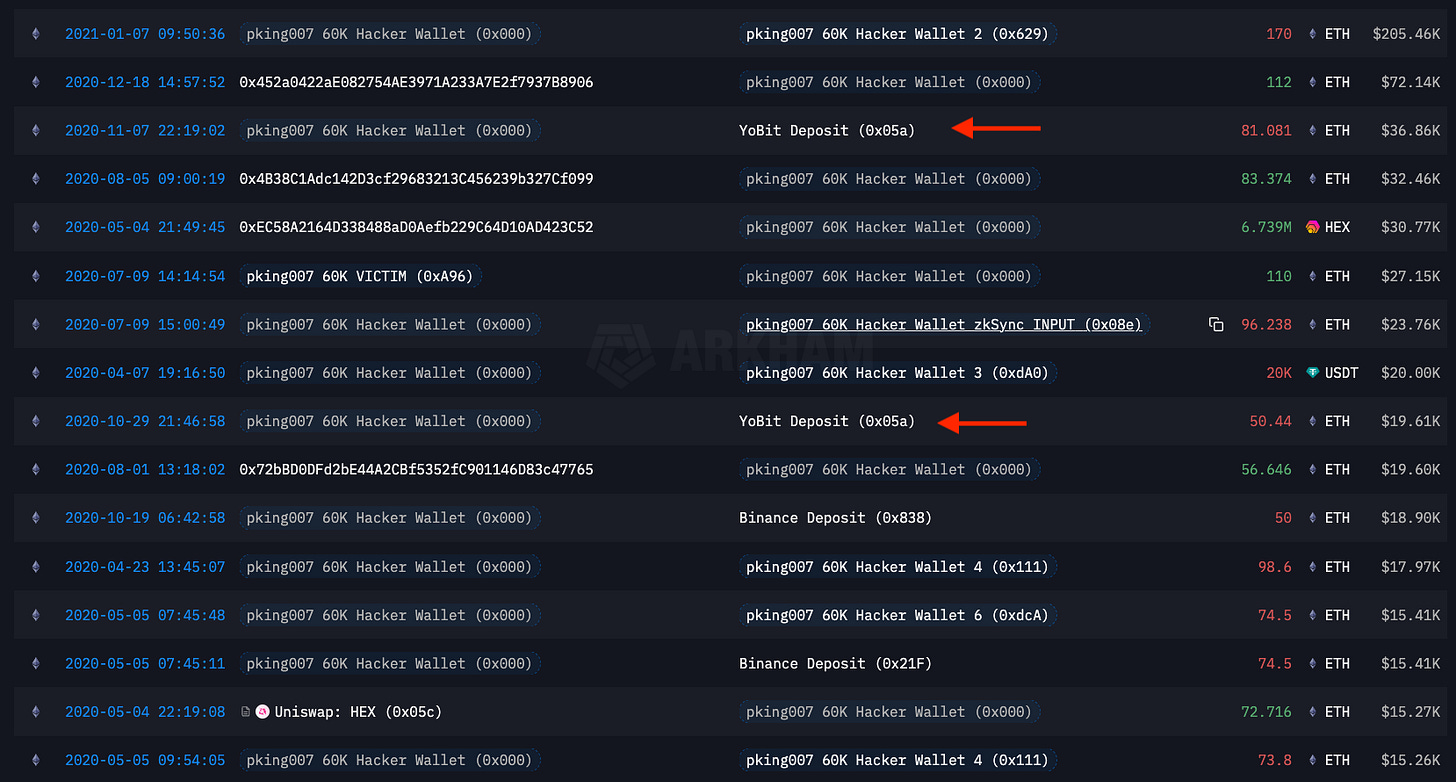
The above image is from the wallet 0x0000000937e390bd7753B2B30a1b2d96154e9Aba, the main ETH wallet involved in the theft.
The top two highest value deposits both go into the Yobit deposit address of 0x05a8fC18C8150cBD6cEc07621dE2aA7c426a21e6 directly from the hacker’s wallet.
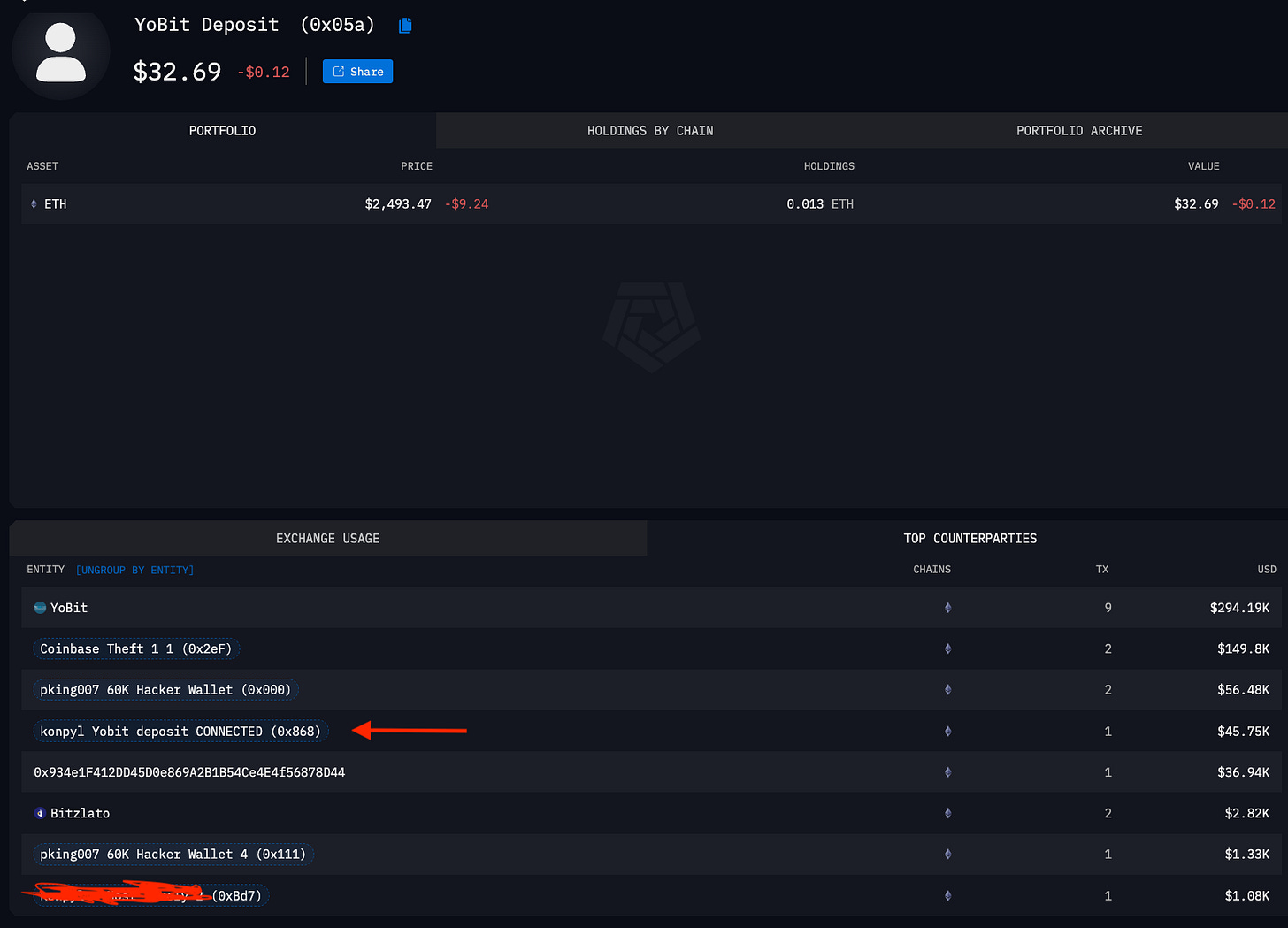
Inside the Yobit deposit address of 0x05a8fC18C8150cBD6cEc07621dE2aA7c426a21e6 I marked off a wallet directly connected to Konstantin’s Main Wallet.
Looking at 0x8683782AB9A71e6B6F410544aC2fd70d8bE6FF5b in the image above labeled konpyl Yobit deposit CONNECTED, I come across yet another Yobit Deposit address of 0x7e179E3DDF5e1f15bFAe4F10715Fda703d3873cE.
271 ETH valued at $678,143.88 was deposited here with this Etherscan transaction.
Who owns the Yobit deposit address of 0x7e179E3DDF5e1f15bFAe4F10715Fda703d3873cE?
It’s clear its a deposit belonging to Konstantin Pylinskiy, konpyl.
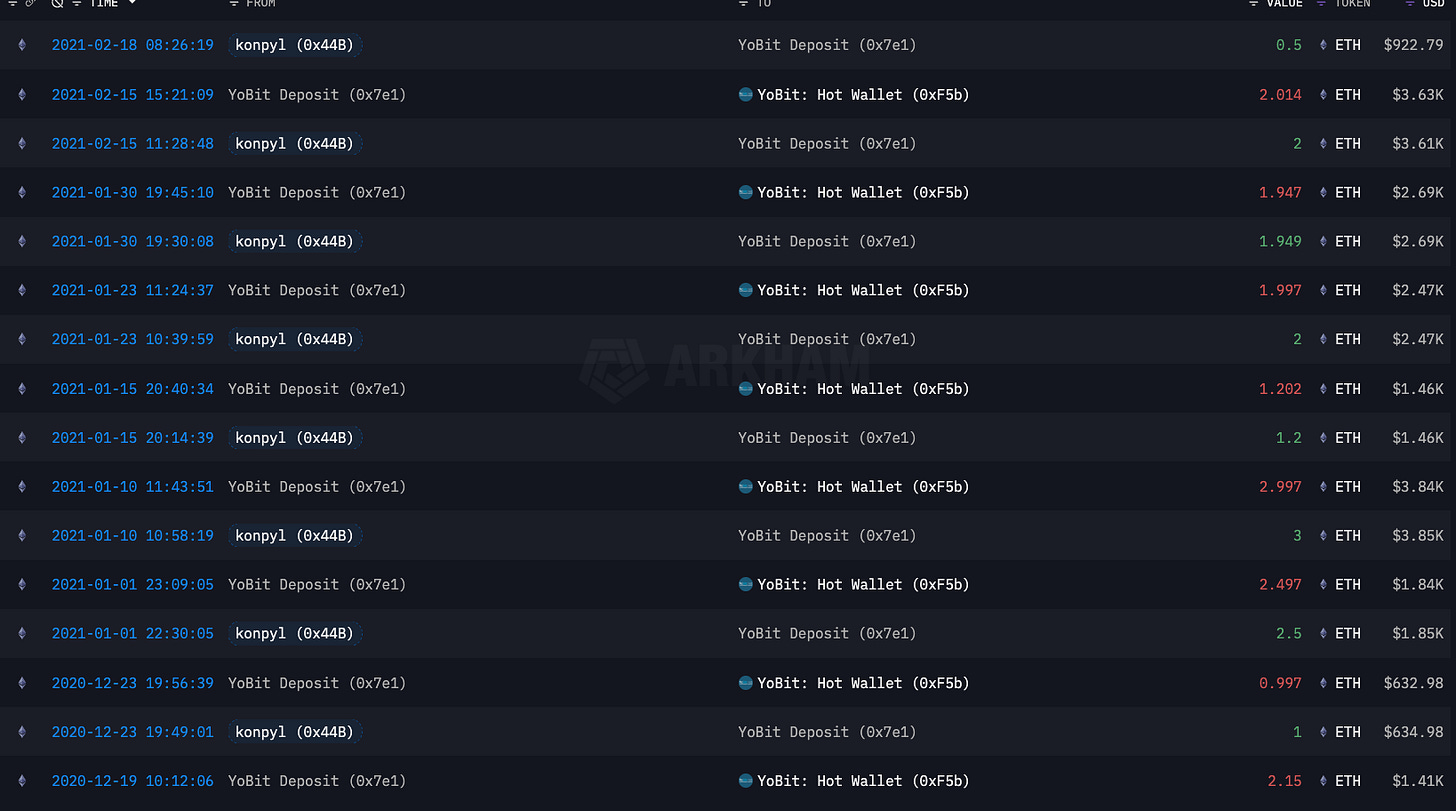
Above is an image of the most recent transactions inside 0x7e179E3DDF5e1f15bFAe4F10715Fda703d3873cE - Yobit. I’m showing 23 txns worth about 41.5K getting deposited from “konpyl’s” main wallet of 0x44BdB19dB1Cd29D546597AF7dc0549e7f6F9E480.
Stay tuned, I'll be sharing more hacks done by Konstantin connected directly to this deposit address.